Risk Assessment Iso 27001.xls
Risk assessment gives a structured idea of evaluating the areas of improvement which needs to be worked upon. Based upon this a comprehensive report analysing the aspect impact can always prove to be handy. In accordance with the same, a risk assessment and treatment report needs to be framed, evaluated, compiled and put to place for an easy reference. This would be time saving and also have subtle advantages like getting the purview of an organisation’s efforts in securing its information and critical assets.
An iso 27001 risk assessment template provides companies with an easy-to-use way to organize all aspects of the project that range from inception to completion. Whether your company is a global player or a smaller actor on the commercial stage, this template should be an indispensable part of your basic reports toolkit as you set about. ISO/IEC A.8.1.1, A.8.1.2. And operational requirements are understood and inform the management of cybersecurity risk. Risk Assessment (ID.RA): The organization understands the cybersecurity risk to organizational operations (including mission, functions, image, or reputation), organizational assets, and individuals. A security risk assessment identifies, assesses, and implements key security controls in applications. It also focuses on preventing application security defects and vulnerabilities. Carrying out a risk assessment allows an organization to view the application.
Kwickcert takes into account the ground level experiences which organizations might encounter and taking them into consideration gives an extensive idea on preparation of such reports. It must include vulnerabilities, threats, severity and possible factors which might hinder the business flow.
KwikCert provides ISO 27001 RISK ASSESSMENT AND TREATMENT REPORT Document Template with Live Expert Support. By using this document you can Implement ISO 27001 yourself without any support. We provide 100% success guarantee for ISO 27001 Certification. Download this ISO 27001 Documentation Toolkit for free today.
This RISK ASSESSMENT AND TREATMENT REPORTDocument Template is part of the ISO 27001 Documentation Toolkit. The toolkit combines documentation templates and checklists that demonstrate how to implement this standard through a step-by-step process. In addition, you can access help from our experts to keep you on the right path, ensuring a straight-forward journey to ISO 27001 certification.
By using this 27001 RISK ASSESSMENT AND TREATMENT REPORT Document Template, you have less documentation to complete, yet still comply with all the necessary guidelines and regulations. The Documentation Template decreases your workload, while providing you with all the necessary instructions to complete this document as part of the ISO 27001 certification requirement.
If yours is a small company looking to implement the ISO 27001 Information Security Management System by applying the mandatory documents required by ISO 27001 requirements, as well as documenting the common non-mandatory procedures, then this is the perfect toolkit. Using this toolkit ensures you are able to conform to the leading Information Security Management System standard: ISO 27001.
Iso 27001 Risk Register
Document Template Features
- Optimized for small and medium-sizedcompanies
- Costs up to 80% less than using consultants
- Expert consultations and unlimited email support available
- Documentation fully editable? – Yes. You can adapt any document by entering specific information for your organization.
- Acceptable for ISO certification audit? – This document template is perfectly acceptable for the certification audit
- Documentation Free? – Yes. Absolutely.
ISO 27001 is the most popular information security standard worldwide, and organisations that have achieved compliance with the Standard can use it to prove that they are serious about the information they handle and use.
ISO 27001 is the globally accepted standard that offers clients the assurance that the organisation is managing the confidentiality, integrity and availability of information.
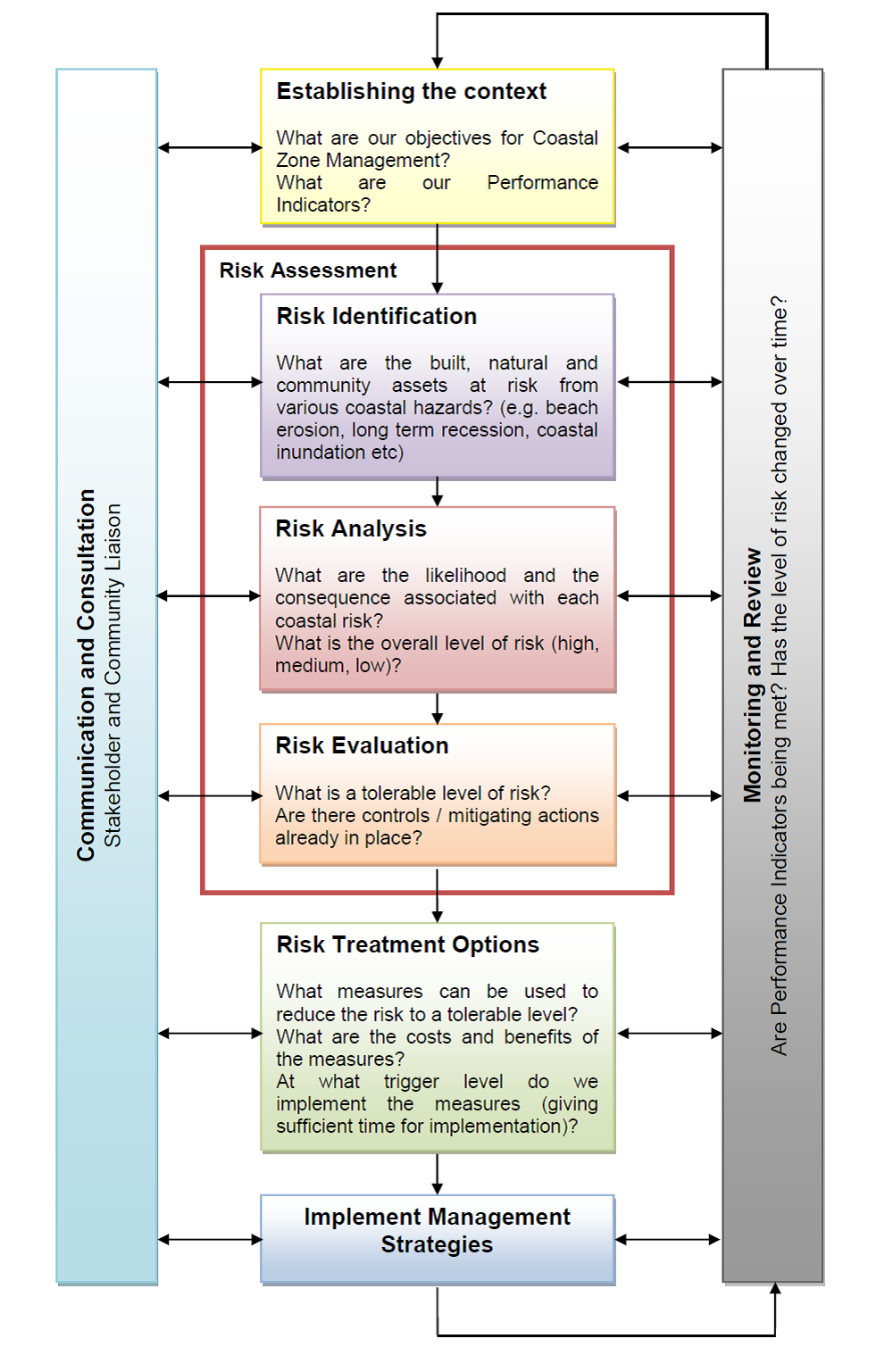
One of the cornerstones of implementing an ISO 27001-compliant ISMS (information security management system) is conducting an effective information security risk assessment.
Mitigate your risks
In order to tackle the risks to your organisation’s information assets, the assessor will usually need to take the following broad steps:
- Identify the various information assets that could be jeopardised.
- Consider the threats that could compromise those assets.
- Assess the vulnerabilities in the organisation that could compound those threats.
- Establish the likelihood and impact of such risks coming to pass.
- Estimate the damage that such threats could bring about.
Once this part of the risk assessment has been completed, the next critical element is to identify and select the relevant controls from Annex A of ISO 27001:2013 (or elsewhere), to ensure that each of the risks has been treated effectively.
Risk management
The organisation may choose to treat, tolerate, transfer or terminate the risk, based on the company’s risk appetite and the total estimation of the risk.
There are, of course, a number of other things that need to be considered throughout the process, such as what the organisation’s risk appetite is, what kind of risk assessment criteria to use, in addition to what risk calculation formula and additional sets of controls to apply.
The easiest way to get this done is with risk assessment template.
With a template, there is no need to compile extensive lists of assets, no need to try and find a library of threats and vulnerabilities (or risks), no need to wonder which threats could affect which assets, and no need to try and think which controls would apply to which risks. With vsRisk™, all of this has already been done for you.
With vsRisk, you can copy, edit and replicate a built-in risk assessment template, populated with the following:
- A library of assets, pre-assigned to organisational roles that typically manage those assets;
- Pre-selected threats and vulnerabilities (risks), applied to each asset group;
- The relevant ISO 27001:2013 controls pre-applied to each risk.
In addition, vsRisk features customisable and editable reports, such the SoA (Statement of Applicability) and Risk Treatment Plan, which are crucial for an ISO 27001 audit.
Looking for more compliance advice?
You can find out more about identifying and evaluating your interested parties with the help of CyberComply.
This Cloud-based collection of information security software helps you take control of your cyber risk needs in one simple package.
Iso 27001 Risk Assessment Methodology
It includes a feature that identifies the relevant legal, contractual and regulatory obligations you need to meet to ensure compliance with the interested parties clause of ISO 27001.
Iso 27001 Risk Assessment Template
A version of this blog was originally published on 18 July 2016.