Advanced Microsoft Office 365 Data Protection
Digital transformation has revolutionized the way organizations operate, improved their productivity, enabled greater collaboration and enhanced business workflows with state-of-the-art technologies like AI. Digital transformation also created new threats of business data leakage as well as new regulations such as the new European Union’s General Data Protection (GDPR) governing how organization should store and protect sensitive business data. More than ever before, data protection is a top of mind for many central IT teams.
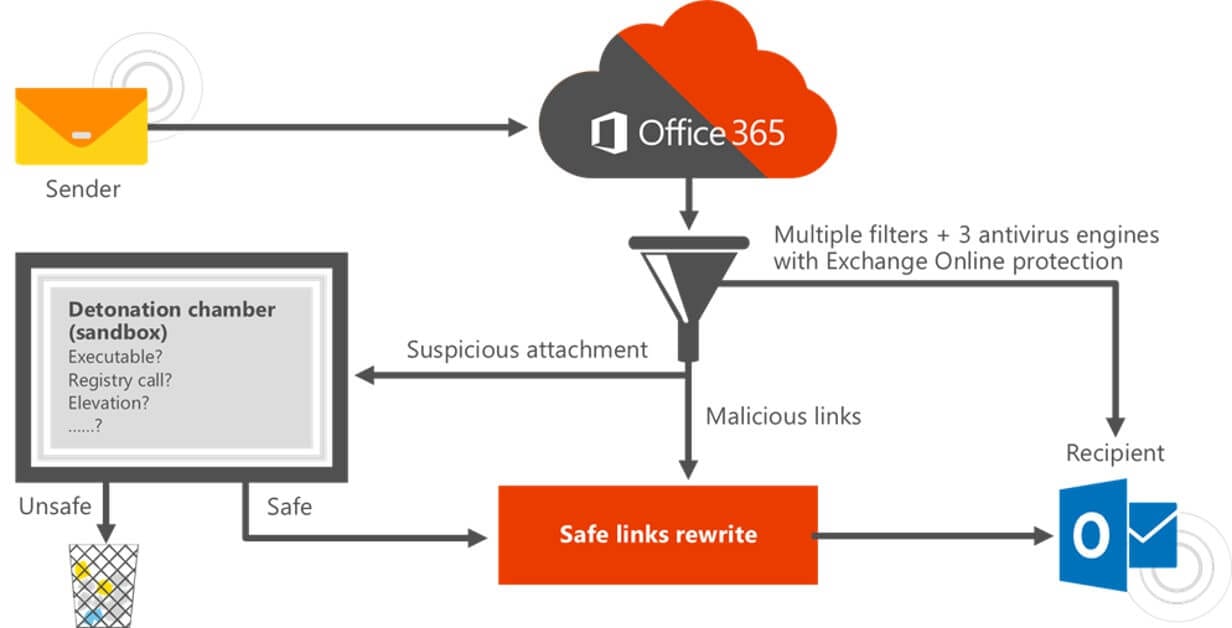
The Microsoft 365 collection of threat-protection technologies helps protect against and provides visibility about spam, malware, viruses, phishing attempts, malicious links, and other threats. Prevent, detect, and respond to advanced threats Get comprehensive endpoint protection with Microsoft Defender Advanced Threat Protection. We are excited to announce new data protection capabilities in Power BI that build on Microsoft’s strengths in security and enable customers to empower every user with Power BI and better protect their data no matter how or where it is accessed. Classify and label sensitive Power BI data using the familiar Microsoft Information Protection sensitivity labels used in Office. Enforce governance.
Power BI adoption by large enterprises is growing very fast. To reduce the risk for data leakage, up until now some organizations have chosen to block export from Power BI and/or limit user access to sensitive data, at the expense of productivity. Others, have chosen just to rely on their employees following the organization’s data protection guidelines, in order to maintain high productivity. Both options require IT teams to make a compromise between data protection and productivity.
Over the past six months, the Power BI team has worked closely with the Microsoft Information Protection and Cloud App Security teams to provide a solution that will enable Power BI customers to have their data protected, while maintaining high productivity.
It is now possible to:
- Classify and label sensitive Power BI data using the familiar Microsoft Information Protection sensitivity labels used in Office.
- Enforce governance policies even when Power BI content is exported to Excel, PowerPoint, or PDF, to help ensure data is protected even when it leaves Power BI.
- Monitor and protect user activity on sensitive data in real time with alerts, session monitoring, and risk remediation using Microsoft Cloud App Security.
- Empower security administrators who use data protection reports and security investigation capabilities with Microsoft Cloud App Security to enhance organizational oversight.
Sensitivity labels in Power BI
A sensitivity label is a tag that you can apply on Power BI datasets, reports, dashboards and dataflows, it is:
- Customizable to the organizations needs – By defining sensitivity labels, organizations can create categories for different levels of sensitive content, such as Personal, Public, General, Confidential, and Highly Confidential.
- Easily visible – It’s easy for content creators to apply sensitive labels as part of the content creation flow. Once the label has been applied any consumer that interacts with the content can see the content sensitivity.
- Persistent – after a sensitivity label has been applied to content in Power BI, it persist applying both the label and protection when it is exported to: Excel, PowerPoint and PDF.
The beauty of this new capability is that these are the same sensitivity labels often used by organizations to classify, label and protect Office 365 files such as Excel, PowerPoint, Word, and Outlook emails.
Once a sensitivity label is applied to a report, Power BI extends applicable protection policies to that report data when it is exported from Power BI to Excel, PowerPoint and PDF files.
For example, if the sensitivity label on a report has a file protection policy, when data is exported from this report to an Excel file, authorized users will be able to view the file, whereas the file is protected against access by unauthorized users.
Authorized users will be able to open the file and see the sensitivity label applied to the Power BI report:
Unauthorized users will not be able to open the file:
Sensitivity labels applied on reports and dashboards are also visible when viewing reports and dashboards in the Power BI mobile app (IOS and Android)
Licenses are required to apply and view sensitivity labels in Power BI and in Office apps.
Real-time controls and monitoring with Microsoft Cloud App Security
Microsoft Cloud App Security is one of the world’s leading cloud access security brokers used to secure the use of cloud apps. It enables organizations to monitor and control, in real time, risky Power BI sessions such as user access from unmanaged devices. Security administrators can define policies to control user actions, such as downloading reports with sensitive information.
For example, if a user connects to Power BI from an unmanaged device, the session can be monitored by Microsoft Cloud App Security’s real-time controls, and risky actions, such as downloading data that has the “Highly Confidential” sensitivity label applied to it, can be blocked in real time.
Additionally, with Microsoft Cloud App Security, administrators have real-time visibility and control over Power BI user activities concerning data that has sensitivity labels. This visibility and control include security alerts for Power BI service activities such as mass or suspicious report sharing (preview), etc.
Microsoft Cloud App Security licenses are required for these capabilities.
Click here to sign-up to data protection webinar.
Coming soon: New protection metrics report for admins in Power BI admin portal
Adapted from https://www.microsoft.com/en-us/education/buy-license/microsoft365/default.aspx, see source for additional details.
| Microsoft 365 A3 | Microsoft 365 A5 | ||
| Collaboration & Learning | Office Online: web-based document editing | X | X |
| Office client applications: Word, Excel, PowerPoint, Outlook | X | X | |
| Email and calendar, instant messenger (IM), persistent chat, Yammer | X | X | |
| Files and content management: file storage, sharing, information discovery, Groups, Planner | X | X | |
| Minecraft: Education Edition with Code Builder | X | X | |
| Classroom Tools | Microsoft Teams with classroom experiences, professional learning communities (PLC), and staff teams | X | X |
| OneNote Class Notebook, Sway | X | X | |
| More inclusive classrooms | Learning Tools, Accessibility Checker, Office Lens | X | X |
| Voice, video & meetings | Skype for Business | X | X |
| PSTN (public switched telephone network) Conferencing, Cloud PBX (private branch exchange) | X | ||
| Compliance | Legal Hold, eDiscovery search and export | X | X |
| Advanced eDiscovery, Customer Lockbox, Advanced Data Governance | X | ||
| Analytics | Delve | X | X |
| Power BI Pro, MyAnalytics | X | ||
| Management & Security | Intune for Education | X | X |
| School Data Sync, Data Loss Prevention, Office 365 Rights Management | X | X | |
| Office 365 A3: Advanced Security Management, Skype Meeting Broadcast | X | X | |
| Enterprise Mobility Suite (EMS) A3: Intune for Education, Azure Active Directory P1, Azure Information Protection P1, Advanced Threat Analytics | X | X | |
| Windows 10 Education A3: Windows Defender Antivirus, Device Guard | X | X | |
| Advanced Security | Office 365 A5: Advanced Threat Prevention, Threat Intelligence | X | |
| Enterprise Mobility Suite (EMS) A5: Azure Active Directory P2, Azure Information Protection P2, Cloud App Security | X | ||
| Windows 10 Education A5: Windows Defender Advanced Threat Protection | X | ||
| Server & CAL Benefits | Productivity Server Licenses and Client Access Licenses (CALs) for Exchange, SharePoint, Skype for Business, etc. | X | X |
| Windows Server Client Access Licenses (CALs) | X | X | |
| System Center Configuration Manager CML | X | X | |
| System Center Endpoint Protection | X | X |
E3 vs E5 comparison
Advanced Microsoft Office 365 Data Protection
Adapted from https://www.microsoft.com/en-us/cloud-platform/enterprise-mobility-security-pricing, see source for additional details
Microsoft 365 Advanced Threat Protection
E3 Mobility | E5 Mobility | ||
| Identity and access management | Simplified access management and security | X | X |
Multi-factor authentication | X | X | |
Conditional access | X | X | |
Risk-based conditional access | X | ||
Advanced security reporting | X | X | |
Privileged identity management | X | ||
Windows Server Client Access License (CAL)* | X | X | |
| Managed mobile productivity | Mobile device management | X | X |
Mobile application management | X | X | |
Advanced Microsoft Office 365 data protection | X | X | |
Integrated PC management | X | X | |
Integrated on-premises management | X | X | |
| Information protection | Persistent data protection | X | X |
Intelligent data classification and labeling | X | ||
Document tracking and revocation | X | X | |
Encryption key management per regulatory needs | X | X | |
| Identity-driven security | Microsoft Advanced Threat Analytics | X | X |
Microsoft Cloud App Security | X | ||
Azure Advanced Threat Protection | X |